Introduction
This post describes TLS configuration for Oracle Enterprise Command Center Framework using self-signed certificates. Configuring TLS is required to secure communication between the Oracle Enterprise Command Center Framework installation and the Oracle E-Business Suite. It is assumed that TLS is already enabled in the EBS instance according to the following document:
Enabling TLS in Oracle E-Business Suite Release 12.2 (Doc ID 1367293.1)
Also it is assumed that the ECC is already installed and configured but without TLS between ECC and EBS.
References
I used the following document as the guideline for the configuration:
Enabling TLS for Oracle Enterprise Command Center Framework, Release 12.2 (Doc ID 2496445.1)
Using EBS with TLS and ECC without TLS
Please note that it is possible to use TLS Enabled EBS and ECC without TLS.
In such case you may face an issue during ECC configuration which is described in the following post. The section is called “Import Enterprise Command Center Applications into TLS enabled EBS instance”.
Apart from that you it is required to set EBS_ parameters according to Doc ID 2496445.1 to the TLS values.
Example:
EBS_MIDDLETIER_HOST_FQDN=demo.enginatics.com EBS_MIDDLETIER_PORT=4443 EBS_MIDDLETIER_PROTOCOL=https |
The ECC_ parameters can be set to the http mode:
ECC_HOST_PROTOCOL=http ECC_HOST_NAME=ecc.localdomain ECC_ADMIN_PORT=7775 ECC_MANAGED_PORT=7776 |
Using EBS and ECC both configured for TLS
Configuring https for the ECC installation
Open $ECC_BASE/Oracle/quickInstall/EccConfig.properties file and update the TLS related properties. Here is the values I set for my system:
EBS_MIDDLETIER_HOST_FQDN=r122.localdomain EBS_MIDDLETIER_PORT=4443 EBS_MIDDLETIER_PROTOCOL=https ECC_HOST_NAME=ecc.localdomain ECC_HOST_PROTOCOL=https ECC_ADMIN_SSL_PORT=7777 ECC_MANAGED_SSL_PORT=7778 |
Source the $ECC_BASE/Oracle/quickInstall/env/ecc.env environment
source $ECC_BASE/Oracle/quickInstall/env/ecc.env |
Stop all ECC processes
$ECC_BASE/Oracle/quickInstall/bin/stopAllEcc.sh |
Apply the changes to the EccConfig.properties by running the following command:
$ECC_BASE/Oracle/quickInstall/wlsScripts/configurePorts.sh $ECC_BASE/Oracle/quickInstall/env/ecc.env $ECC_SERVER_DOMAIN |
I faced the following error during the above script execution:
Error: setListenPort() failed. Do dumpStack() to see details.
Error: set() failed. Do dumpStack() to see details.
Error: runCmd() failed. Do dumpStack() to see details.
com.oracle.cie.domain.script.jython.WLSTException
at com.oracle.cie.domain.script.jython.CommandExceptionHandler.handleException(CommandExceptionHandler.java:69)
at com.oracle.cie.domain.script.jython.WLScriptContext.handleException(WLScriptContext.java:3085)
at com.oracle.cie.domain.script.jython.WLScriptContext.runCmd(WLScriptContext.java:738)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at org.python.core.PyReflectedFunction.__call__(Unknown Source)
at org.python.core.PyMethod.__call__(Unknown Source)
at org.python.core.PyObject.__call__(Unknown Source)
at org.python.core.PyInstance.invoke(Unknown Source)
at org.python.pycode._pyx5.command$1(/tmp/WLSTOfflineIni3600317565071631640.py:19)
at org.python.pycode._pyx5.call_function(/tmp/WLSTOfflineIni3600317565071631640.py)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyFunction.__call__(PyFunction.java:188)
at org.python.pycode._pyx5.set$15(/tmp/WLSTOfflineIni3600317565071631640.py:79)
at org.python.pycode._pyx5.call_function(/tmp/WLSTOfflineIni3600317565071631640.py)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyFunction.__call__(PyFunction.java:184)
at org.python.pycode._pyx33.f$0(/u01/Oracle/software/temp/configureSSLPorts.py:20)
at org.python.pycode._pyx33.call_function(/u01/Oracle/software/temp/configureSSLPorts.py)
at org.python.core.PyTableCode.call(Unknown Source)
at org.python.core.PyCode.call(Unknown Source)
at org.python.core.Py.runCode(Py.java:1226)
at org.python.util.PythonInterpreter.execfile(Unknown Source)
at weblogic.management.scripting.WLST.main(WLST.java:186)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at weblogic.WLST.main(WLST.java:47)
Caused by: com.oracle.cie.domain.script.ScriptException
at com.oracle.cie.domain.script.jython.WLSTState.processCommand(WLSTState.java:243)
at com.oracle.cie.domain.script.jython.WLScriptContext.runCmd(WLScriptContext.java:732)
... 31 more
Caused by: com.oracle.cie.domain.script.jython.WLSTException
at com.oracle.cie.domain.script.jython.CommandExceptionHandler.handleException(CommandExceptionHandler.java:69)
at com.oracle.cie.domain.script.jython.WLScriptContext.handleException(WLScriptContext.java:3085)
at com.oracle.cie.domain.script.jython.WLScriptContext.set(WLScriptContext.java:2532)
at com.oracle.cie.domain.script.jython.WLScriptContext.set(WLScriptContext.java:2568)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at com.oracle.cie.domain.script.jython.WLSTState.processCommand(WLSTState.java:226)
... 32 more
Caused by: java.lang.reflect.InvocationTargetException
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at com.oracle.cie.domain.script.jython.WLScriptContext.set(WLScriptContext.java:2528)
... 38 more
Caused by: java.lang.reflect.UndeclaredThrowableException
at com.sun.proxy.$Proxy47.setListenPort(Unknown Source)
... 43 more
Caused by: com.oracle.cie.domain.script.jython.WLSTException: 64016: Attempt to set disabled property.
64016: The property "SSL Listen Port" is disabled on type SSL.
64016: Internal error. No user actions available.
at com.oracle.cie.domain.script.jython.CommandExceptionHandler.handleException(CommandExceptionHandler.java:69)
at com.oracle.cie.domain.script.jython.WLScriptContext.handleException(WLScriptContext.java:3085)
at com.oracle.cie.domain.script.jython.ScriptInvocationHandler.invoke(ScriptInvocationHandler.java:236) |
Fix as per Doc ID 2495053.1:
Note: During the execution of the restore.sh script, the following exception may occur:
Caused by: com.oracle.cie.domain.aspect.ConfigAspectValidateException: 64016: Attempt to set disabled property. 64016: The property "SSL Listen Port" is disabled on type SSL. 64016: Internal error. No user actions available |
This is an expected behavior and does not need any action from the administrator.
Start all the ECC components
$ECC_BASE/Oracle/quickInstall/bin/startAllEcc.sh |
Select option 1 – All
Integrate the updated Oracle Enterprise Command Center Framework installation with EBS
$ECC_BASE/Oracle/quickInstall/envSetup.sh |
Select option 5 – Integrate With EBS
Enabling tls for the oracle enterprise command center framework installation
For this conifguration I used a self-signed certificate.
Source the ECC environment
source $ECC_BASE/Oracle/quickInstall/env/ecc.env |
Create a new directory for the keystore for the Oracle Enterprise Command Center Framework managed server
cd $ECC_BASE/Oracle/Middleware/ mkdir keystores cd keystores |
Create a new keystore that contains a private key and self-signed certificate for the Oracle ECC managed server
keytool -genkeypair -alias wlskey -keyalg "RSA" -sigalg SHA256withRSA -keysize 2048 -keystore weblogic.jks -validity [validity_period_in_days] -dname "CN=[common_name], OU=[organizational_unit], O=[organization_name], ST=[state], C=[country]" |
Example:
keytool -genkeypair -alias wlskey -keyalg "RSA" -sigalg SHA256withRSA -keysize 2048 -keystore weblogic.jks -validity 3650 -dname "CN=ecc.localdomain, OU=Development, O=Enginatics, ST=Zurich, C=CH" |
Enter the new keystore passwords when prompted.
Convert the JKS keystore file to a file in the P12 format.
keytool -importkeystore -srckeystore weblogic.jks -destkeystore ecc_ca_interim.p12 -srcstoretype jks -deststoretype pkcs12 |
Enter the source and destination keystores passwords when prompted. The ecc_ca_interim.p12 file is created as the result of this command.
Export the certificate as a file in the PEM format.
openssl pkcs12 -in ecc_ca_interim.p12 -nokeys -clcerts -out ecc_ca_interim.pem |
Enter the P12 keystore password when prompted.
Remove the bag attributes from the file to extract only the certificate itself.
openssl x509 -in ecc_ca_interim.pem -out ecc_ca.pem |
When prompted, enter the P12 keystore password. The resulting ecc_ca.pem file will be copied to the EBS host later.
Configuring the ECC Managed Server for TLS with a Self-signed Certificate
Log in to the Oracle Enterprise Command Center Framework domain admin console at the following URL:
<ECC_HOST_PROTOCOL>://<ECC_HOST_NAME>:<ECC_ADMIN_PORT>/console |
E.g.:
http://ecc.localdomain:7775/console |
In the left pane of the Console, expand Environment and select Servers.
Click the name of the Oracle WebLogic Server instance for Oracle Enterprise Command Center Framework, such as eccManaged.
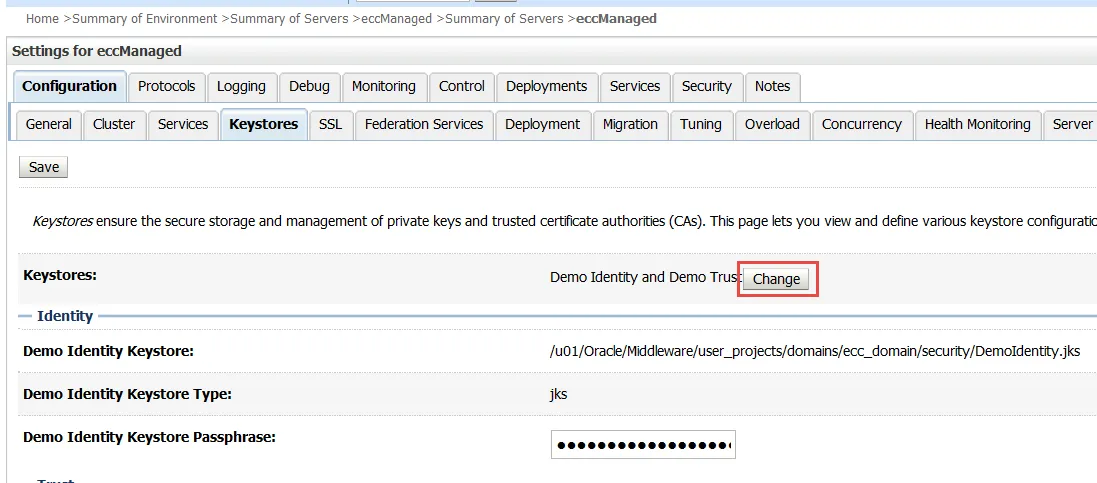
Select Configuration > Keystores. In the Keystores tab, click Lock & Edit and set the following values.
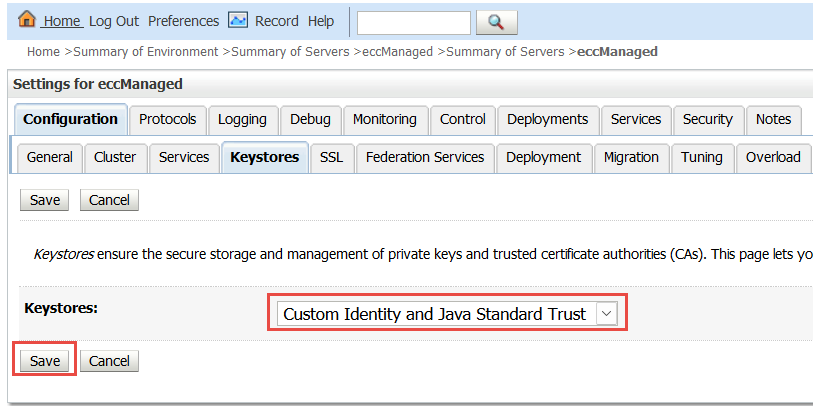
For the Keystores option, click Change and select Custom Identity and Java Standard Trust. Then click Save.
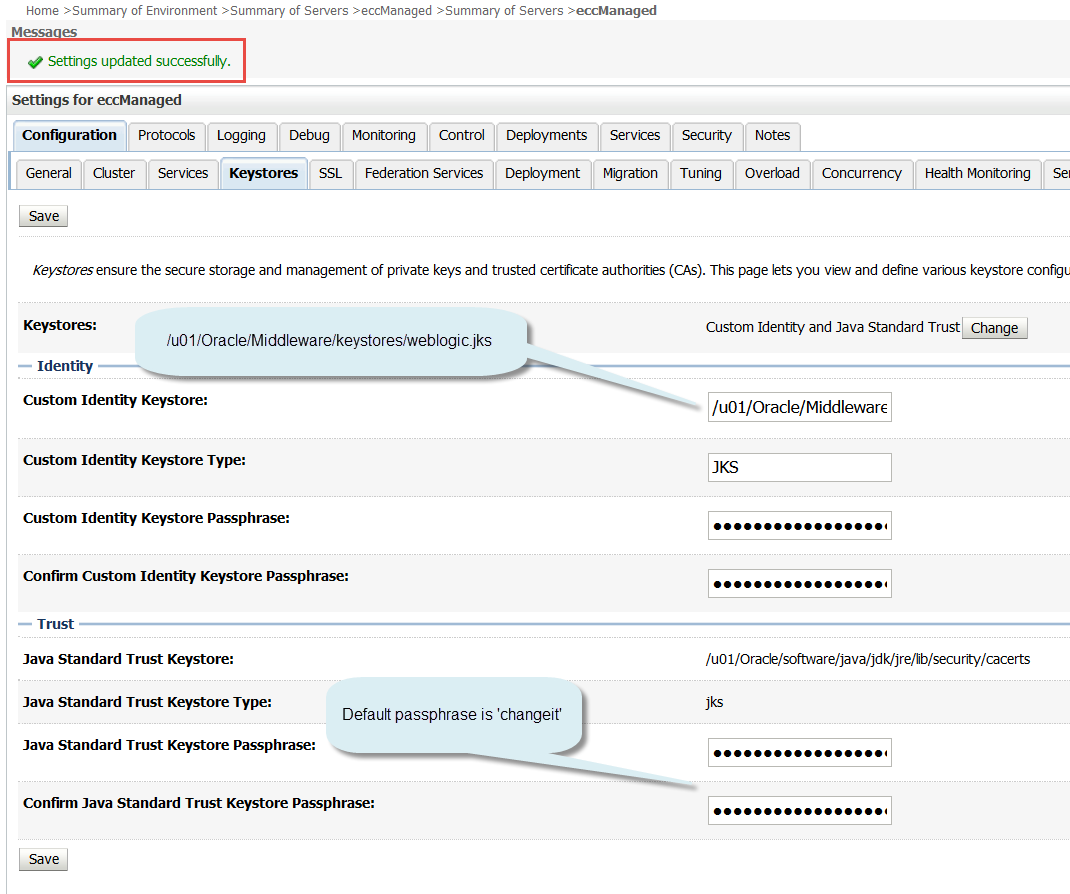
In the Custom Identity Keystore option, specify the full path to the location of the weblogic.jks file. For example:
/u01/Oracle/Middleware/keystores/weblogic.jks |
Set the Custom Identity Keystore Type field to JKS.
In the Custom Identity Keystore Passphrase field and the Confirm Custom Identity Keystore Passphrase field, enter the WLS keystore password that you specified when you created the weblogic.jks keystore.
The Java Standard Trust Keystore is set by default to the location of the cacerts file for your environment.
The Java Standard Trust Keystore Type is set by default to JKS.
In the Java Standard Trust Keystore Passphrase field and the Confirm Java Standard Trust Keystore Passphrase field, enter the passphrase for the cacerts file. The default password/passphrase for the cacerts is ‘changeit’ per this documentation.
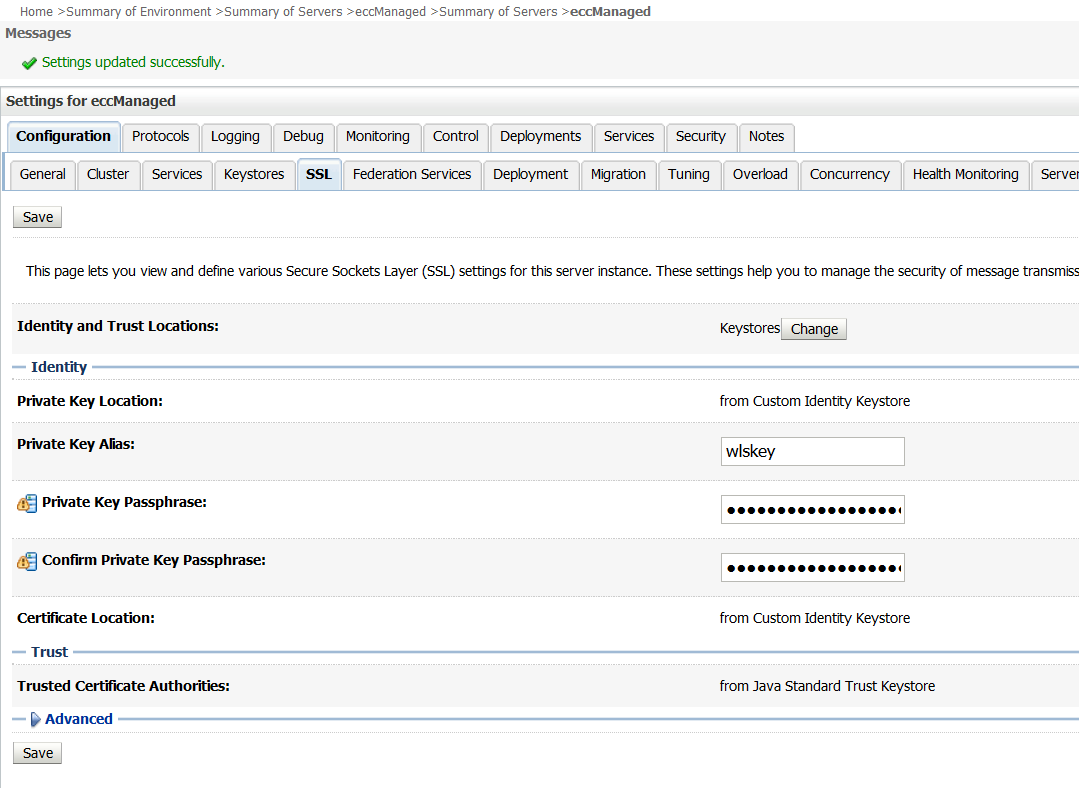
Select the SSL tab and set the following values.
Check that the Trusted Certificate Authorities option is set to From Java Standard Trust Keystore.
Set the Private Key Alias field to wlskey.
In the Private Key Passphrase field and the Confirm Private Key Passphrase field, enter the WLS key password that you specified when you created the weblogic.jks keystore.
Click Save.
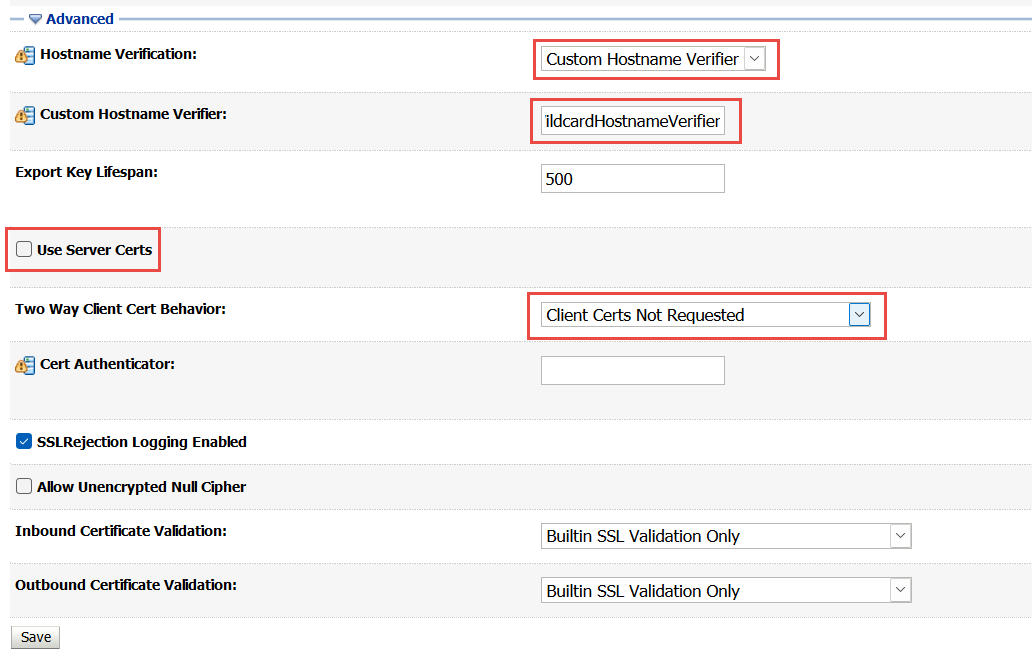
Click the Advanced link.
Change the value of the Hostname Verification field to Custom Hostname Verifier and the value of the Custom Hostname Verifier field to weblogic.security.utils.SSLWLSWildcardHostnameVerifier.
Ensure that the Use Server Certs check box is deselected.
In the Two Way Client Cert Behavior option, select Client Certs Not Requested.
Click Save.
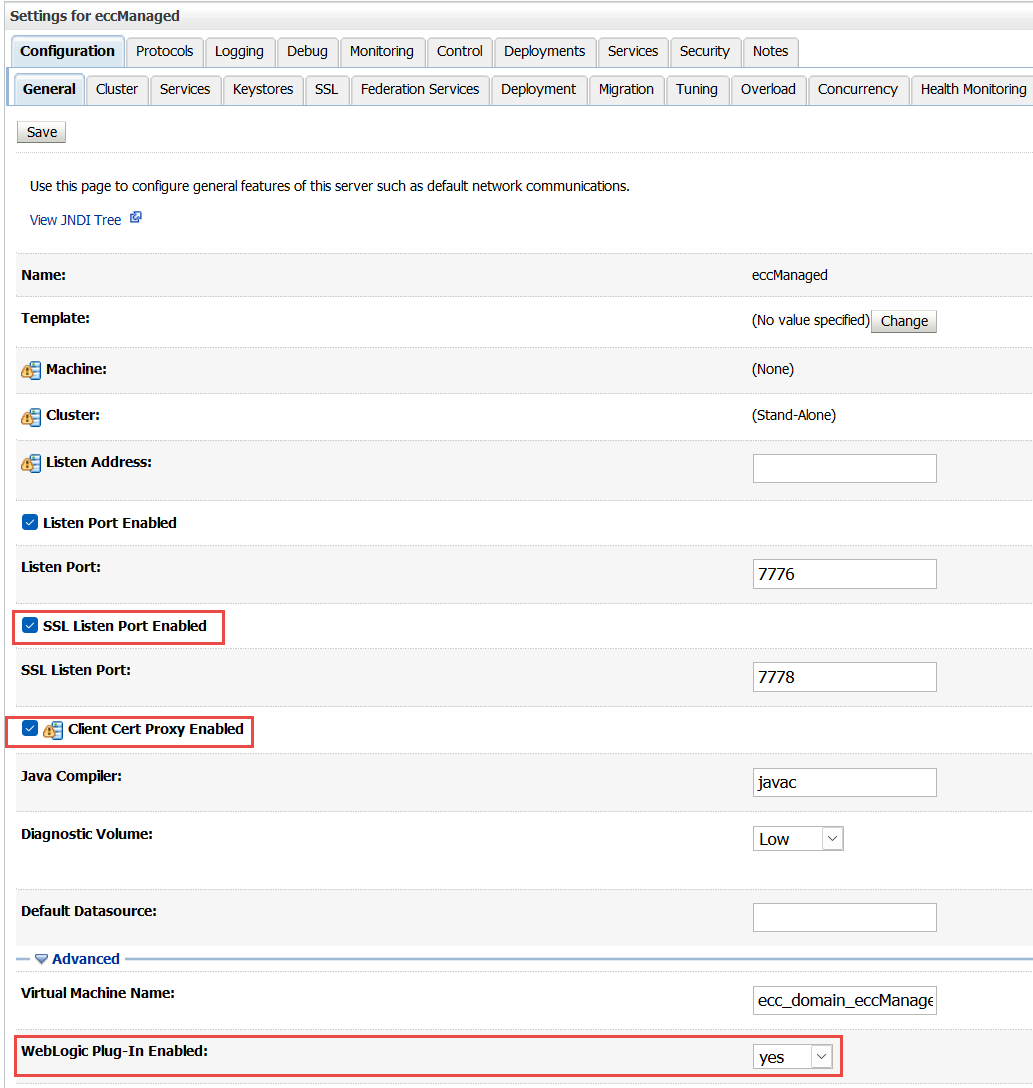
Select the General tab and set the following values.
Ensure that the SSL Listen Port Enabled option is selected. Set the port value to an available port in your environment, that is, a port that is not already in use. Then click Save.
Select the Client Cert Proxy Enabled check box. Then click Save.
Click the Advanced link. In the WebLogic Plug-In Enabled option, select Yes. Then click Save.
In the Change Center pane of the console, click Activate Changes.
The following confirmation message appears: All changes have been activated. However 1 item must be restarted for the changes to take effect.
Importing the Self-signed Certificate for the ECC Managed Server into the Java Standard Trust Keystore
Import the self-signed certificate into the Java Standard Trust Keystore in the cacerts file.
Back up the current cacerts file. First, change to the directory where the cacerts file is located.
cd [Java_Standard_Trust_Keystore_location] |
E.g.:
cd $ECC_BASE/Oracle/software/java/jdk/jre/lib/security |
Then create a backup copy of the file.
cp cacerts cacerts_backup |
Import the certificate from the Oracle Enterprise Command Center Framework Managed Server keystore into the cacerts file. First, change to the directory you created for the keystore.
cd $ECC_BASE/Oracle/Middleware/keystores |
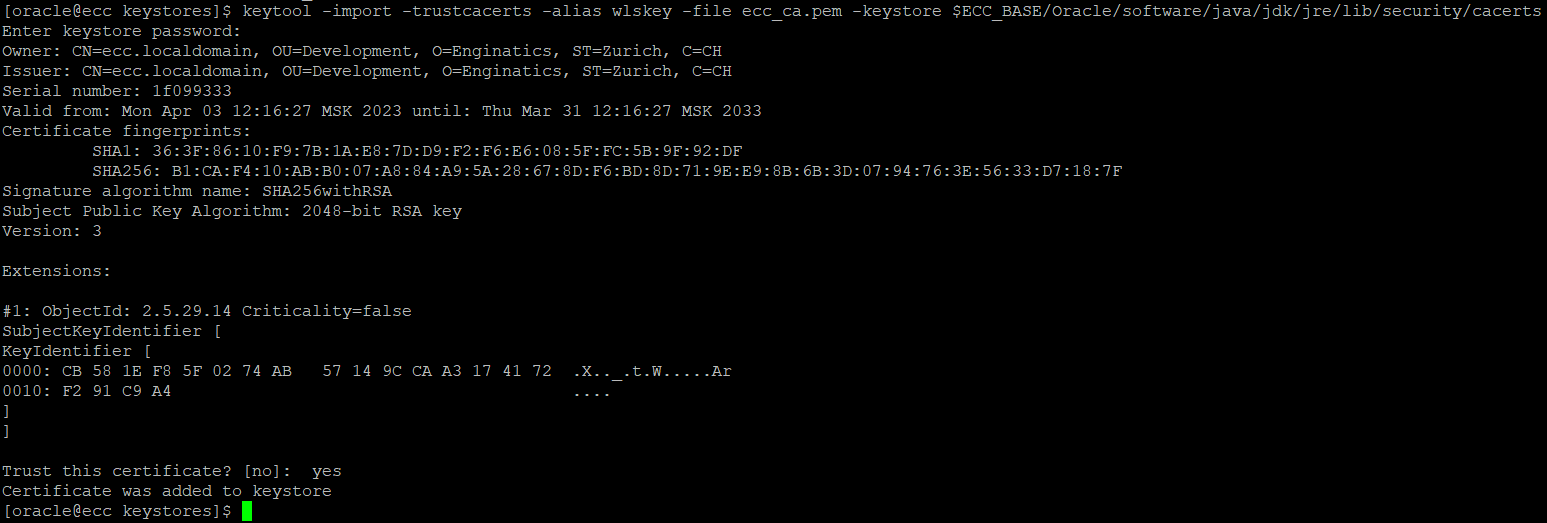
Then use keytool to import the certificate.
keytool -import -trustcacerts -alias wlskey -file ecc_ca.pem -keystore [Java_Standard_Trust_Keystore_location] |
E.g.:
keytool -import -trustcacerts -alias wlskey -file ecc_ca.pem -keystore $ECC_BASE/Oracle/software/java/jdk/jre/lib/security/cacerts |
When prompted, enter the keystore password for the cacerts file. The default password is ‘changeit’.
At the prompt Trust this certificate? [no], enter y.
The following confirmation message appears: Certificate was added to keystore
Configuring Strong Ciphers for the Oracle Enterprise Command Center Framework Managed Server
Secure the Oracle Enterprise Command Center Framework managed server with a restricted cipher list in the config.xml file.
Change to the directory where the config.xml file is located.
cd $ECC_BASE/Oracle/Middleware/user_projects/domains/ecc_domain/config |
Open the config.xml file in a text editor and locate the following lines:
> eccManaged</name> <ssl> <enabled>true</enabled> ... |
Add the following directives after the <enabled>true</enabled> directive.
<ciphersuite>TLS_RSA_WITH_AES_256_CBC_SHA</ciphersuite> <ciphersuite>TLS_RSA_WITH_AES_128_CBC_SHA</ciphersuite> <ciphersuite>TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256</ciphersuite> <ciphersuite>TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384</ciphersuite> |
The resulting entries in the config.xml file should appear as follows:
> eccManaged</name> <ssl> <enabled>true</enabled> <ciphersuite>TLS_RSA_WITH_AES_256_CBC_SHA</ciphersuite> <ciphersuite>TLS_RSA_WITH_AES_128_CBC_SHA</ciphersuite> <ciphersuite>TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256</ciphersuite> <ciphersuite>TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384</ciphersuite> ... |
Enabling TLS for the ECC Domain
Enable TLS for the ECC domain by adding the TLSv1.2 protocol entry in the setDomainEnv.sh file for the ECC domain.
Change to the directory where the setDomainEnv.sh file is located.
cd $ECC_BASE/Oracle/Middleware/user_projects/domains/ecc_domain/bin |
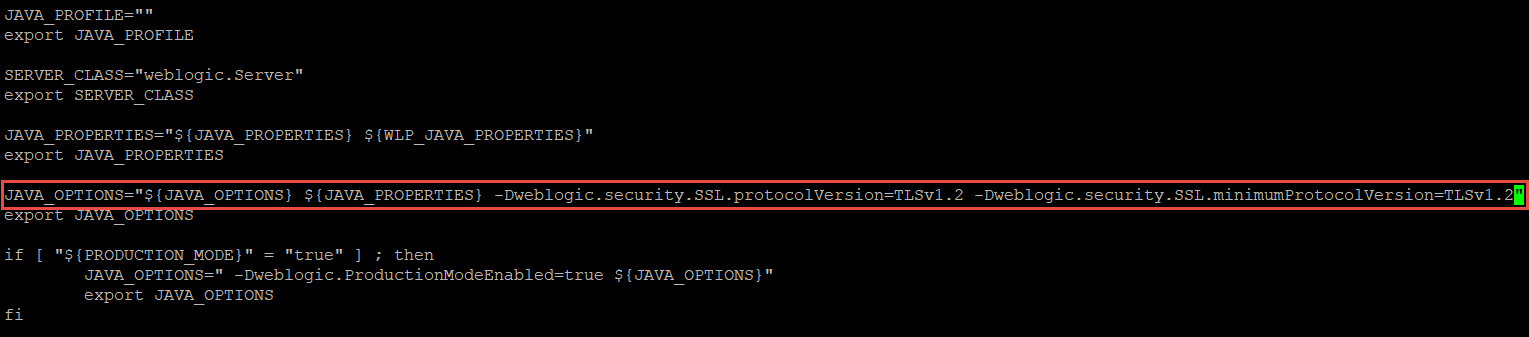
Open the setDomainEnv.sh file in a text editor and locate the following line:
JAVA_OPTIONS="${JAVA_OPTIONS} ${JAVA_PROPERTIES}" |
Replace that line with the following:
JAVA_OPTIONS="${JAVA_OPTIONS} ${JAVA_PROPERTIES} -Dweblogic.security.SSL.protocolVersion=TLSv1.2 -Dweblogic.security.SSL.minimumProtocolVersion=TLSv1.2" |
Restart the All the ECC processes using the following scripts:
$ECC_BASE/Oracle/quickInstall/bin/stopAllEcc.sh $ECC_BASE/Oracle/quickInstall/bin/startAllEcc.sh |
Updating the Oracle WebLogic Server Security Filters
Perform the following steps to update the Oracle WebLogic security filters for Oracle Enterprise Command Center Framework.
Log in to the Oracle WebLogic Server admin console at the following URL:
<ECC_HOST_PROTOCOL>://<ECC_HOST_NAME>:<ECC_ADMIN_PORT>/console |
E.g.:
http://ecc.localdomain:7775/console |
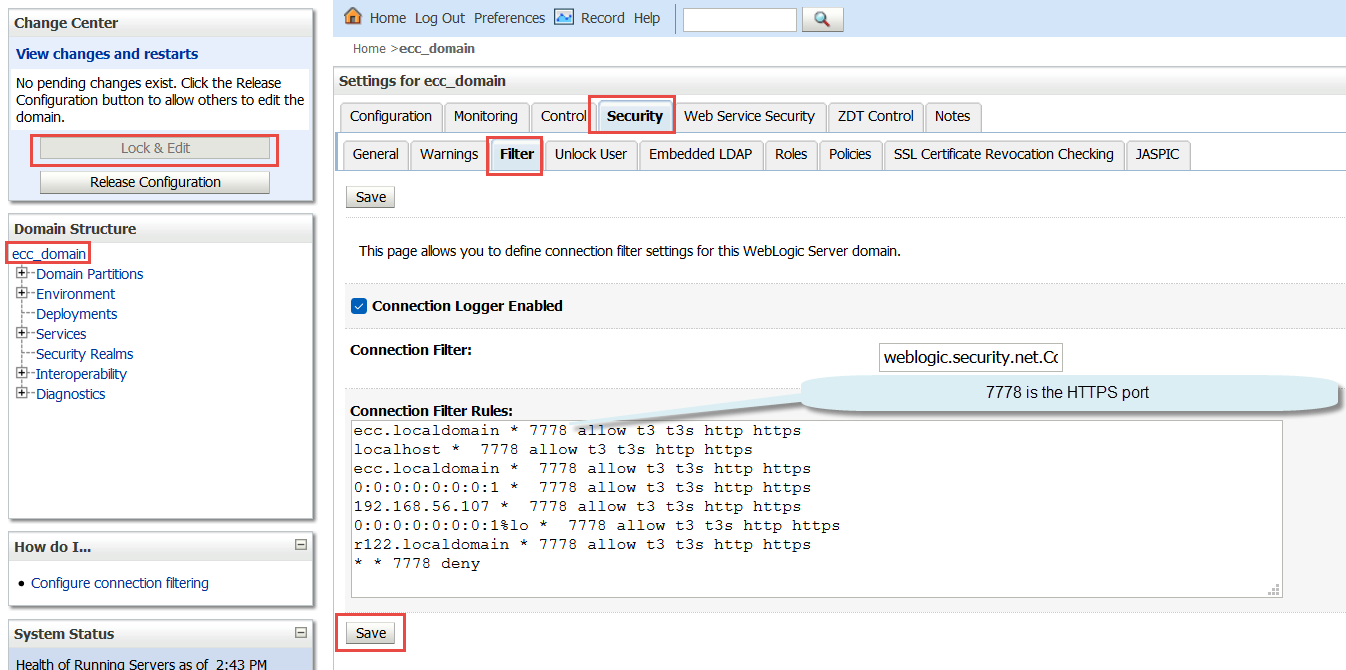
Click the Lock & Edit button.
In the Domain Structure section, select ecc_domain.
Click the Security tab, and then click the Filter tab.
In the Connection Filter Rules field, select and copy all the existing rules.
Paste the rules into a temporary text file. In the temporary file, replace the HTTP port in each rule with the port used for HTTPS. Then copy the updated rules.
Return to the Filter tab and add the updated rules in the Connection Filter Rules field by pasting them after the end of the original list of rules. Do not overwrite the original rules.
Click the Save button.
Click the Activate Changes button.
Configuring Oracle EBS for https connections to the oracle ECC
Source the environment file for the run filesystem
$ . EBSapps.env run |
Check and write down the values of the following variables:
grep -i s_web_ssl_directory $CONTEXT_FILE grep -i s_ohs_instance_loc $CONTEXT_FILE grep -i s_ohs_component $CONTEXT_FILE |
You may export the following variables with the returned values for convenience. E.g.
export s_web_ssl_directory=/u01/install/APPS/fs_ne/inst/EBSDB_apps/certs export s_ohs_instance_loc=/u01/install/APPS/fs1/FMW_Home/webtier/instances/EBS_web_OHS1 export s_ohs_component=EBS_web |
Add the following directory to the PATH variable:
export PATH=$FMW_HOME/webtier/bin:$PATH |
Import the self-signed ECC certificate to the EBS wallet
You can skip this step if you used a PKI certificate signed by a commercial CA.
Copy the ecc_ca.pem certificate file that you created for the Oracle ECC to the Oracle EBS ${s_web_ssl_directory}/Apache directory.
Run the following command to add the certificate to the wallet:
$FMW_HOME/oracle_common/bin/orapki wallet add -wallet ./ -trusted_cert -cert ecc_ca.pem -auto_login_only |
Modifying the Oracle HTTP Server Wallet after importing the self-signed ECC certificate
You can skip this step if you used a PKI certificate signed by a commercial CA.
Navigate to the
${s_ohs_instance_loc}/config/OHS/${s_ohs_component}/keystores/default |
directory.
Move the existing wallet files to a backup directory.
Copy the cwallet.sso file from the
${s_web_ssl_directory}/Apache |
directory into the current directory. E.g.:
cd ${s_ohs_instance_loc}/config/OHS/${s_ohs_component}/keystores/default
cp ${s_web_ssl_directory}/Apache/cwallet.sso . |
Adding TLS Directives to the ecc.conf File
Perform the following steps to update the ecc.conf file with the required TLS directives.
Navigate to the
${s_ohs_instance_loc}/config/OHS/${s_ohs_component}/ |
directory
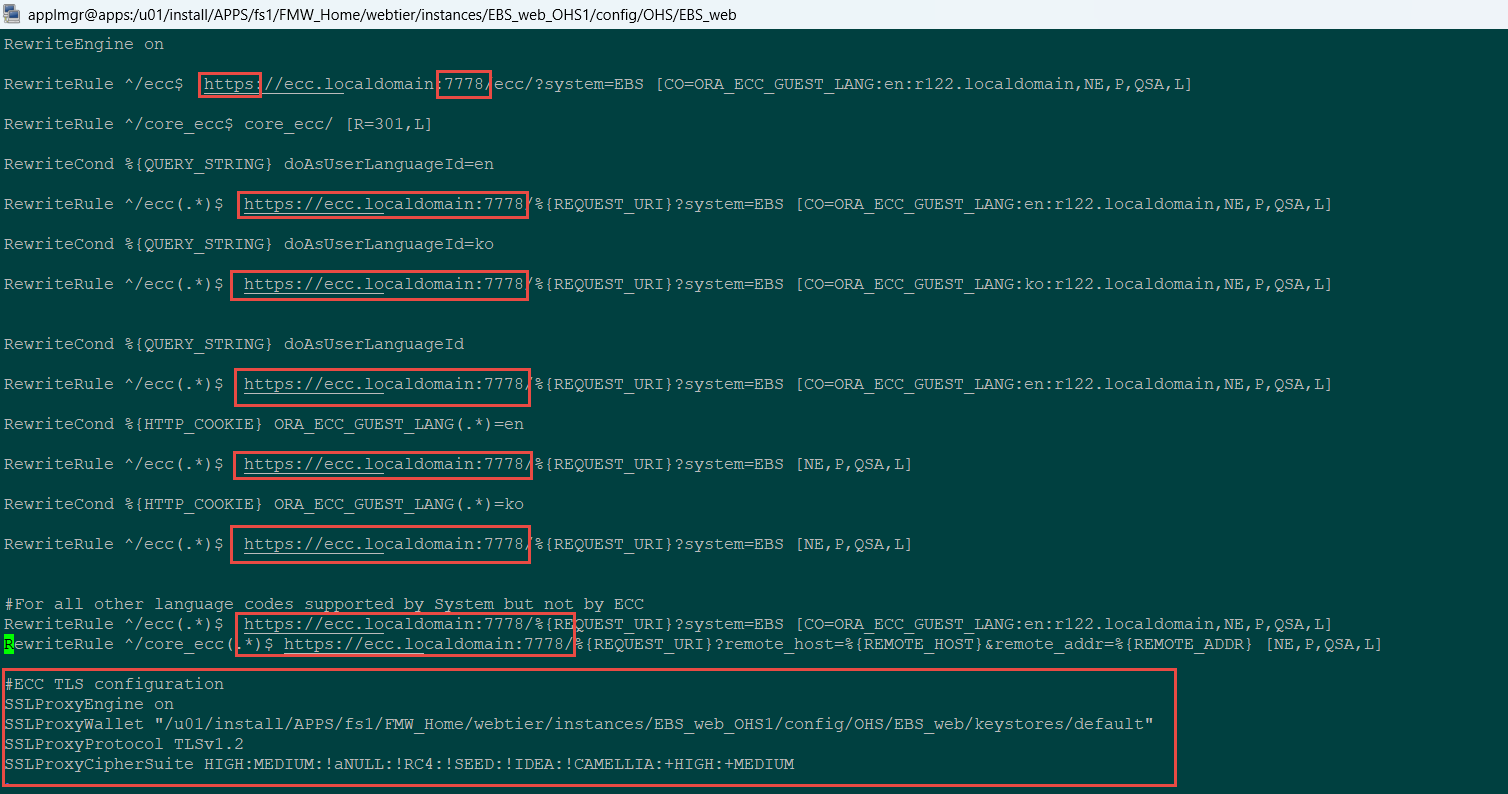
Open the ecc.conf file in a text editor and add the following directives:
SSLProxyEngine on
SSLProxyWallet "${s_ohs_instance_loc}/config/OHS/${s_ohs_component}/keystores/default"
SSLProxyProtocol TLSv1.2
SSLProxyCipherSuite HIGH:MEDIUM:!aNULL:!RC4:!SEED:!IDEA:!CAMELLIA:+HIGH:+MEDIUM |
For example:
SSLProxyEngine on SSLProxyWallet "/u01/install/APPS/fs1/FMW_Home/webtier/instances/EBS_web_OHS1/config/OHS/EBS_web/keystores/default" SSLProxyProtocol TLSv1.2 SSLProxyCipherSuite HIGH:MEDIUM:!aNULL:!RC4:!SEED:!IDEA:!CAMELLIA:+HIGH:+MEDIUM |
Verify that all the Oracle Enterprise Command Center Framework URLs in the ecc.conf file use the protocol https and the appropriate port for HTTPS connections.
Perform the same steps on the patch filesystem.
Disabling Automatic Update of the ecc.conf File
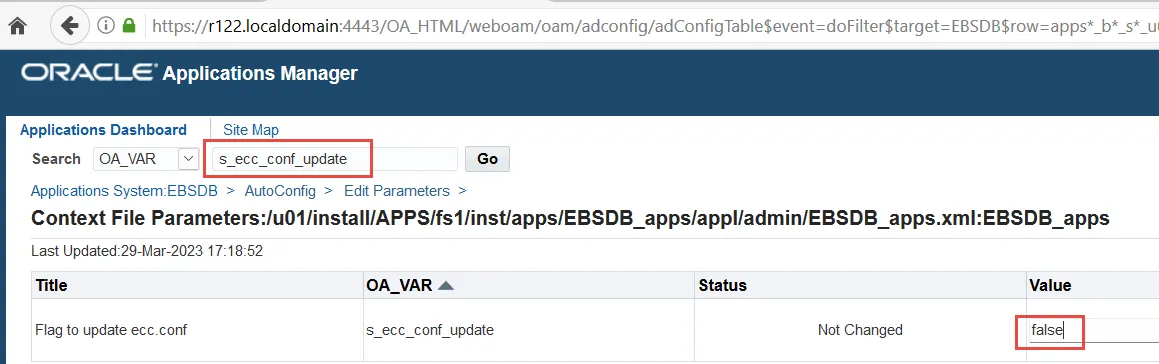
In Oracle Applications Manager, update the Oracle E-Business Suite context file to ensure that the ecc.conf file will not be updated automatically. This change is required to preserve your manual updates.
Log in to Oracle E-Business Suite as a system administrator.
Navigate to System Administration: Oracle Applications Manager > AutoConfig.
Select the application tier context file, and choose Edit Parameters.
Search for the s_ecc_conf_update variable by selecting OA_VAR in the search list of values and entering s_ecc_conf_update in the search text box. Then choose the Go button.
Set the Value field for the s_ecc_conf_update variable to false to ensure that the ecc.conf file will not be updated automatically when AutoConfig is run. Then choose the Save button.
Verify TLS connection to ECC
After the ECC TLS is complete, log in to EBS and navigate to a ECC dashboard. Confirm that the dashboard content appears correctly. For example Payables Command Center:





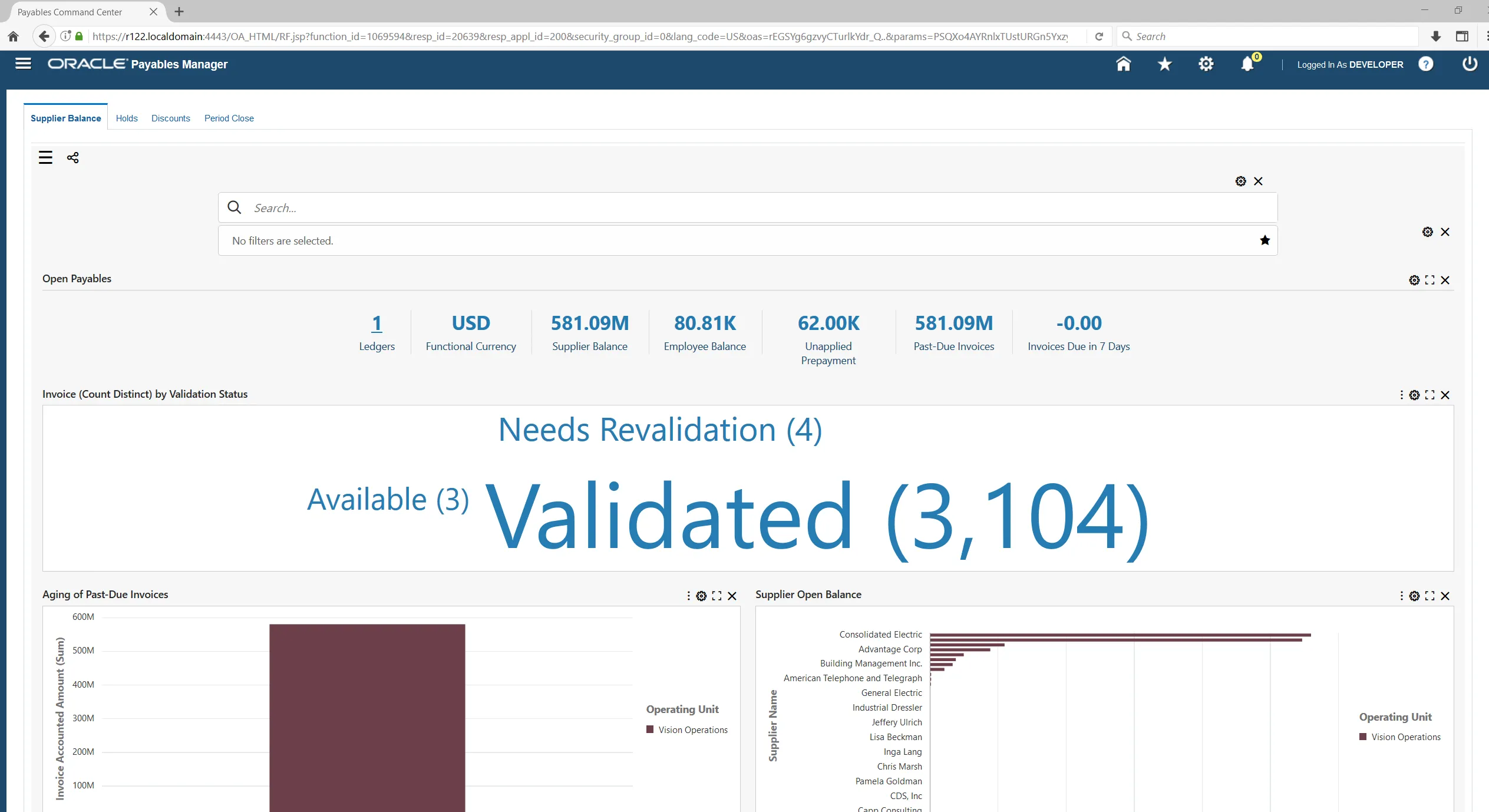
Importing application file name wip_ecc.zip
Importing application /tmp/patchEccFiles_1695276069/wip/12.0.0/patch/115/ecc/applications/wip_ecc.zip
ECC WEB ENTRY URL:https://xxxx.abcd.com:4410/ecc
ECC Application File:/tmp/patchEccFiles_1695276069/wip/12.0.0/patch/115/ecc/applications/wip_ecc.zip
javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No name matching xxxx.abcd.com found
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192)
at sun.security.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1897)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:300)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:294)
at sun.security.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1604)
at sun.security.ssl.ClientHandshaker.processMessage(ClientHandshaker.java:220)
at sun.security.ssl.Handshaker.processLoop(Handshaker.java:1009)
at sun.security.ssl.Handshaker.process_record(Handshaker.java:930)
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1026)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1325)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1352)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1336)
at sun.net.www.protocol.https.HttpsClient.afterConnect(HttpsClient.java:559)
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(AbstractDelegateHttpsURLConnection.java:185)
at sun.net.www.protocol.http.HttpURLConnection.getOutputStream(HttpURLConnection.java:1177)
at sun.net.www.protocol.https.HttpsURLConnectionImpl.getOutputStream(HttpsURLConnectionImpl.java:264)
at oracle.ecc.client.util.ApplicationImporter.importApplication(ApplicationImporter.java:107)
at oracle.ecc.client.ECCClient.main(ECCClient.java:110)
Caused by: java.security.cert.CertificateException: No name matching xxxx.abcd.com found
at sun.security.util.HostnameChecker.matchDNS(HostnameChecker.java:256)
at sun.security.util.HostnameChecker.match(HostnameChecker.java:97)
Import of applications failed
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:353)
at sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:211)
at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:134)
at sun.security.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1586)
… 13 more
ERROR: Importing application /tmp/patchEccFiles_1695276069/wip/12.0.0/patch/115/ecc/applications/wip_ecc.zip failed
Hi Raju
The issue may be related to the self-signed certificates
You need to review the doc:
Enabling TLS in Oracle E-Business Suite Release 12.2 (Doc ID 1367293.1)
The self-signed certificates need to be added to many places like cacerts files
ou may also refer to this document
https://www.enginatics.com/blog/configuring-tls-https-for-oracle-ebs-integrated-soa-gateway-isg-in-12-2
It is for the different product, but involves the similar TLS configuration
ls -l $ORACLE_HOME/sysman/config/b64InternetCertificate.txtcd $ORACLE_HOME/sysman/config/
cp b64InternetCertificate.txt backup_b64InternetCertificate.txt
cat ca.crt>> $ORACLE_HOME/sysman/config/b64InternetCertificate.txt
cd $COMMON_TOP/util/jdk64/jre/lib/security
cp cacerts backup_cacerts
keytool -import -alias Customer_dev -v -keystore cacerts -file ca.crt
cd $OA_JRE_TOP/lib/security
cp cacerts backup_cacerts
keytool -import -alias Customer_dev -v -keystore cacerts -file ca.crt
Thank you,
Alex
I am getting the following error, whilst attempting to import the applications into ECC
cd $FND_TOP/bin
perl patchEccFiles.pl
Importing application /u01/app/DEV/ecc_tmp/wip/12.0.0/patch/115/ecc/applications/wip_gnt_ecc.zip
ECC WEB ENTRY URL:https://ebshost.xxxxx.local:4443/ecc
ECC Application File:/u01/app/DEV/ecc_tmp/wip/12.0.0/patch/115/ecc/applications/wip_gnt_ecc.zip
javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No name matching ebshost.xxxxx.local found
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192)
at sun.security.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1897)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:300)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:294)
at sun.security.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1604)
at sun.security.ssl.ClientHandshaker.processMessage(ClientHandshaker.java:220)
at sun.security.ssl.Handshaker.processLoop(Handshaker.java:1009)
at sun.security.ssl.Handshaker.process_record(Handshaker.java:930)
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1026)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1325)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1352)
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1336)
at sun.net.www.protocol.https.HttpsClient.afterConnect(HttpsClient.java:559)
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(AbstractDelegateHttpsURLConnection.java:185)
at sun.net.www.protocol.http.HttpURLConnection.getOutputStream(HttpURLConnection.java:1177)
at sun.net.www.protocol.https.HttpsURLConnectionImpl.getOutputStream(HttpsURLConnectionImpl.java:264)
at oracle.ecc.client.util.ApplicationImporter.importApplication(ApplicationImporter.java:107)
at oracle.ecc.client.ECCClient.main(ECCClient.java:110)
Caused by: java.security.cert.CertificateException: No name matching ebshost.xxxxx.local found
at sun.security.util.HostnameChecker.matchDNS(HostnameChecker.java:256)
at sun.security.util.HostnameChecker.match(HostnameChecker.java:97)
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:353)
at sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:211)
at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:134)
TLS is enabled within EBS and we don’t TLS enabled on ECC.
Have you ever seen this error?
Regards,
Micky
Hi Micky
Please check if the following MOS document helps:
patchEccFiles.pl Script To Import Applications Fails With “javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No name matching Found” Error (Doc ID 2984426.1)
Thank you,
Alex