Introduction
Oracle E-Business Suite Integrated SOA Gateway configuration for release EBS 12.1 is outlined in the Doc ID 556540.1 and this Enginatics blog post. However additional steps are required if your EBS instance is configured for TLS. This post will show an example of such configuration.
If the TLS configuration is not performed you may face the following issues during the ISG service deployment:
SystemError: Error while sending message to server. sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target |
References
Enabling TLS in Oracle E-Business Suite Release 12.1 (Doc ID 376700.1)
12.1.3 SOA Gateway SSL setups (Doc ID 2192365.1)
Perform steps from the Doc ID 376700.1, section “5.3 Configure Loopback and Outbound Connections”
This section is often overlooked and may cause issues with ISG. Please review it and perform the necessary configuration.
Perform steps from the Doc ID 376700.1, section “7.3 Service Invocation Framework – SOA”
Apply Patch 25034687 R12.OWF.B using adpatch.
[applmgr@r12 tmp]$ cd $ADMIN_SCRIPTS_HOME/ [applmgr@r12 scripts]$ ./adstpall.sh [applmgr@r12 scripts]$ sqlplus -s apps/***** @$AD_TOP/patch/115/sql/adsetmmd.sql ENABLE [applmgr@r12 tmp]$ unzip p25034687_R12.OWF.B_R12_LINUX.zip [applmgr@r12 tmp]$ cd 25034687 [applmgr@r12 25034687]$ adpatch u25034687.drv [applmgr@r12 scripts]$ sqlplus -s apps/***** @$AD_TOP/patch/115/sql/adsetmmd.sql DISABLE |
Apply Patch 22612527 to the 10.1.3.5 home.
[applmgr@r12 tmp]$ unzip p22612527_101350_Generic.zip [applmgr@r12 tmp]$ cd 22612527/ [applmgr@r12 22612527]$ export ORACLE_HOME=$IAS_ORACLE_HOME [applmgr@r12 22612527]$ export PATH=$ORACLE_HOME/OPatch:$PATH [applmgr@r12 22612527]$ which opatch /u01/oracle/VIS/apps/tech_st/10.1.3/OPatch/opatch [applmgr@r12 22612527]$ echo $ORACLE_HOME /u01/oracle/VIS/apps/tech_st/10.1.3 [applmgr@r12 22612527]$ opatch apply |
Update the 32-bit JDK 7 under $OA_JRE_TOP with the Java Cryptography Extension (JCE) updates.
Check the java version:
$OA_JRE_TOP/bin/java -version java version "1.7.0_261" Java(TM) SE Runtime Environment (build 1.7.0_261-b07) Java HotSpot(TM) Server VM (build 24.261-b07, mixed mode) |
JCE was added by default in Java 7 Jan-2018,
So if your java version is 1.7.0.171 or later you can skip this step as this version was released on 2018-01-16 according to the java version history.
Also per Doc ID 556540.1 it is required to upgrade to the latest Java 7.0 update
Using Oracle Applications Manager, update the following context variables:
s_afjsmarg = -Dhttps.protocols=TLSv1.2 or -Dhttps.protocols=TLSv1.0,TLSv1.1,TLSv1.2. The choice of setting here will depend on the protocol set in Section 5.3, Step 1 or Section 6.1.2. s_proxyhost = fully qualified host.domain name s_proxyport = port value s_proxybypassdomain = domain name (Example example.com) s_nonproxyhosts = wildcard domain name (Example *.example.com) s_ssl_truststore = $OA_JRE_TOP/lib/security/cacerts s_ssl_truststoretype = JKS s_ssl_trustmanageralgorithm = SunX509 (For IBM AIX, set the value to "IbmX509" instead.) |
Here is the example for my system. I used command line to simplify the updates of the variables:
update_var()
{
printf "\nUpdating variable $2 in context file $1 with value: $3 "
$COMMON_TOP/util/jdk/jre/bin/java -classpath $CLASSPATH oracle.apps.ad.context.UpdateContext $1 $2 $3
printf "\n"
}
{
update_var $CONTEXT_FILE "s_afjsmarg" TLSv1.2
update_var $CONTEXT_FILE "s_proxyhost" r12.localdomain
update_var $CONTEXT_FILE "s_proxyport" 4443
update_var $CONTEXT_FILE "s_proxybypassdomain" localdomain
update_var $CONTEXT_FILE "s_nonproxyhosts" *.localdomain
update_var $CONTEXT_FILE "s_ssl_truststore" $OA_JRE_TOP/lib/security/cacerts
update_var $CONTEXT_FILE "s_ssl_truststoretype" JKS
update_var $CONTEXT_FILE "s_ssl_trustmanageralgorithm" SunX509
} |
Perform steps from the Doc ID 2192365.1
Apply the October 2015 CPU to the Oracle Fusion Middleware 10.1.3 Oracle Home
<< The minimum CPU requirement for the Oracle Fusion Middleware 10.1.3.5 is the October 2015 CPU level (Patch 21845960).
[applmgr@r12 tmp]$ unzip p21845960_101350_LINUX.zip [applmgr@r12 tmp]$ cd 21845960/ [applmgr@r12 21845960]$ export ORACLE_HOME=$IAS_ORACLE_HOME [applmgr@r12 21845960]$ export PATH=$ORACLE_HOME/OPatch:$PATH [applmgr@r12 21845960]$ which opatch /u01/oracle/VIS/apps/tech_st/10.1.3/OPatch/opatch [applmgr@r12 21845960]$ echo $ORACLE_HOME /u01/oracle/VIS/apps/tech_st/10.1.3 [applmgr@r12 21845960]$ opatch napply |
Disable Older SSL Protocols and Weak Ciphers
Enabling SSL/TLS in Oracle E-Business Suite Release 12, Section 9 (Note 376700.1).
– TLS 1.0, 1.1, and 1.2 are certified.
– use openssl or java keytool to generate the CSR if CSR is needed.
If JRE 1.8 is used then apply Patch 19568561 to the 10.1.3 home
[applmgr@r12 tmp]$ unzip p19568561_10105_LINUX.zip [applmgr@r12 tmp]$ cd 19568561/ [applmgr@r12 19568561]$ export ORACLE_HOME=$IAS_ORACLE_HOME [applmgr@r12 19568561]$ export PATH=$ORACLE_HOME/OPatch:$PATH [applmgr@r12 19568561]$ export OPATCH_PLATFORM_ID=46 [applmgr@r12 19568561]$ which opatch /u01/oracle/VIS/apps/tech_st/10.1.3/OPatch/opatch [applmgr@r12 19568561]$ echo $ORACLE_HOME /u01/oracle/VIS/apps/tech_st/10.1.3 [applmgr@r12 19568561]$ opatch apply |
Update context variables
The following variables have already been updated: s_ssl_truststore, s_ssl_truststoretype and s_ssl_trustmanageralgorithm.
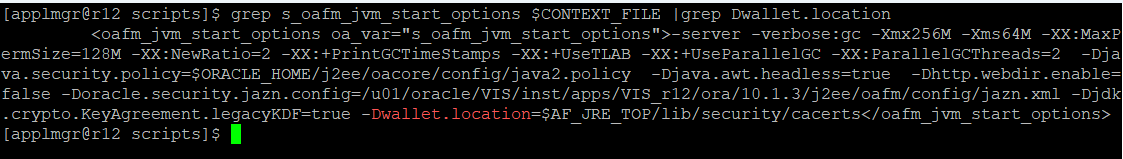
Also change the OA_VAR “s_oafm_jvm_start_options”, so that at the end of this context variable value, the entire location from the value of the “s_ssl_truststore” is present. For example: -Dwallet.location=$AF_JRE_TOP/lib/security/cacerts
Update the template file for oc4j.properties
This step is required because the password is not maintained by Autoconfig so that will need to be manually managed in the oc4j.properties.
To avoid adding the parameter after each Autoconfig run you may create a custom template.
mkdir -p $FND_TOP/admin/template/custom cp $FND_TOP/admin/template/oafm_oc4j_properties_1013.tmp $FND_TOP/admin/template/custom cd $FND_TOP/admin/template/custom vi oafm_oc4j_properties_1013.tmp |
Add the following parameter:
javax.net.ssl.trustStorePassword=changeit |
Run AutoConfig on the apps tier
[applmgr@r12 appl]$ cd $ADMIN_SCRIPTS_HOME/ [applmgr@r12 scripts]$ ./adautocfg.sh |
Verify that oc4j.properties was updated by autoconfig correctly
The $INST_TOP/ora/10.1.3/j2ee/oafm/config/oc4j.properties file contains the values that point to the new jdk keystore:
The values should equal the following:
javax.net.ssl.trustStoreType=JKS javax.net.ssl.trustStore=$AF_JRE_TOP/jre/lib/security/cacerts test.trustmanager.algorithm=Sunx509 #this maybe different depending on the Keystore Provider |
This variable should be inherited from the template file:
javax.net.ssl.trustStorePassword=changeit |
this is the default password, if yours is different then change it here, as the password is not maintained by Autoconfig so that will need to be added manually and managed in the oc4j.properties or added to the template as shown above.
Restart the applications
[applmgr@r12 appl]$ cd $ADMIN_SCRIPTS_HOME/ [applmgr@r12 scripts]$ ./adstpall.sh [applmgr@r12 scripts]$ ./adstrtal.sh |